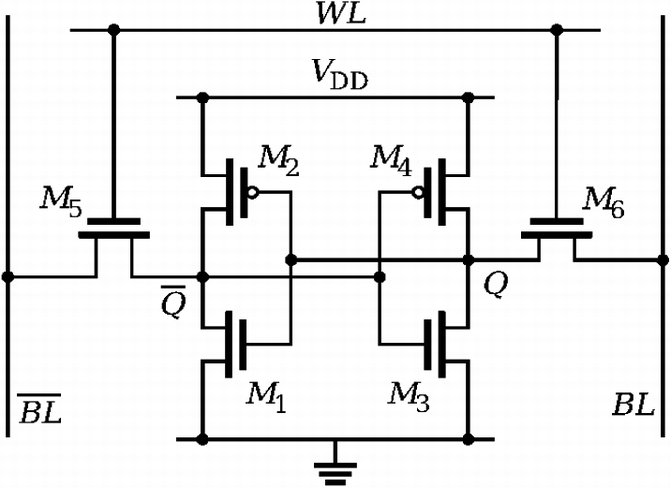
Figure 2 from Design of SRAM PUF with improved uniformity and reliability utilizing device aging effect | Semantic Scholar

Memory based CMOS PUFs: (a) SRAM PUF, (b) latch PUF, and (c) butterfly PUF. | Download Scientific Diagram
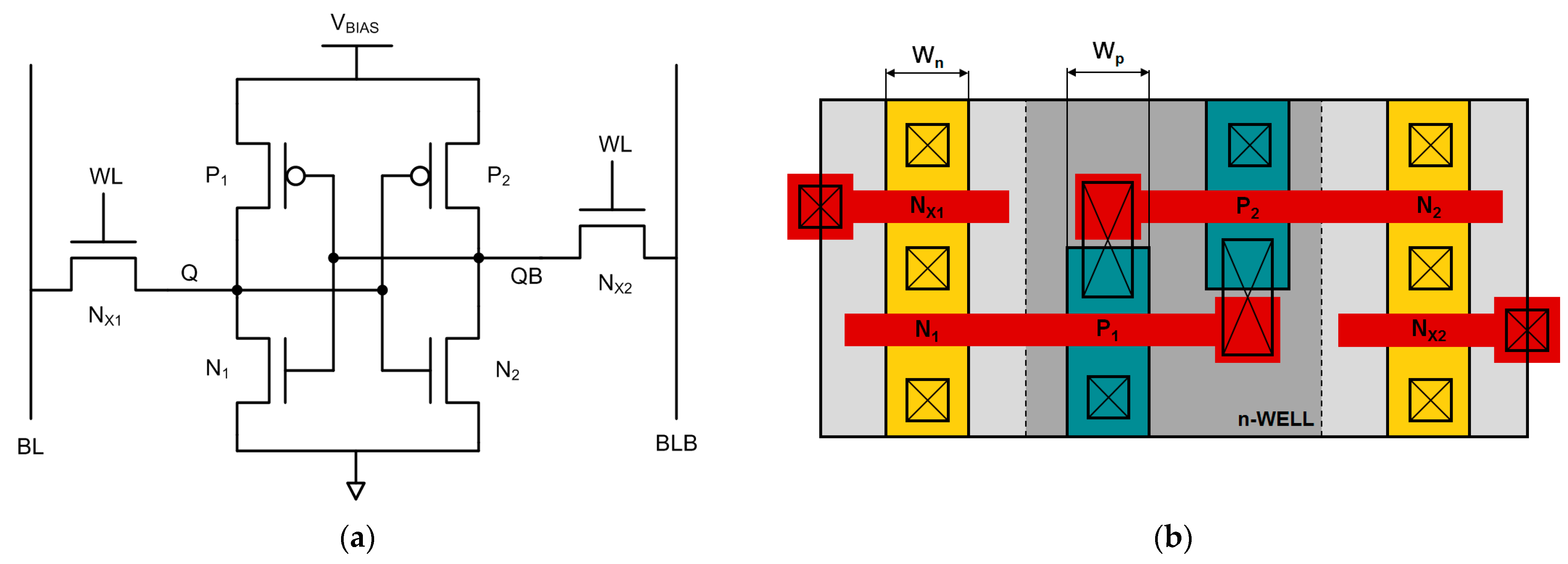
Electronics | Free Full-Text | SRAM-Based PUF Reliability Prediction Using Cell-Imbalance Characterization in the State Space Diagram | HTML